The Integration Crisis Breaking Email Security

Disjointed tools and poor interoperability aren’t just operational headaches—they’re critical vulnerabilities in your email security ecosystem.
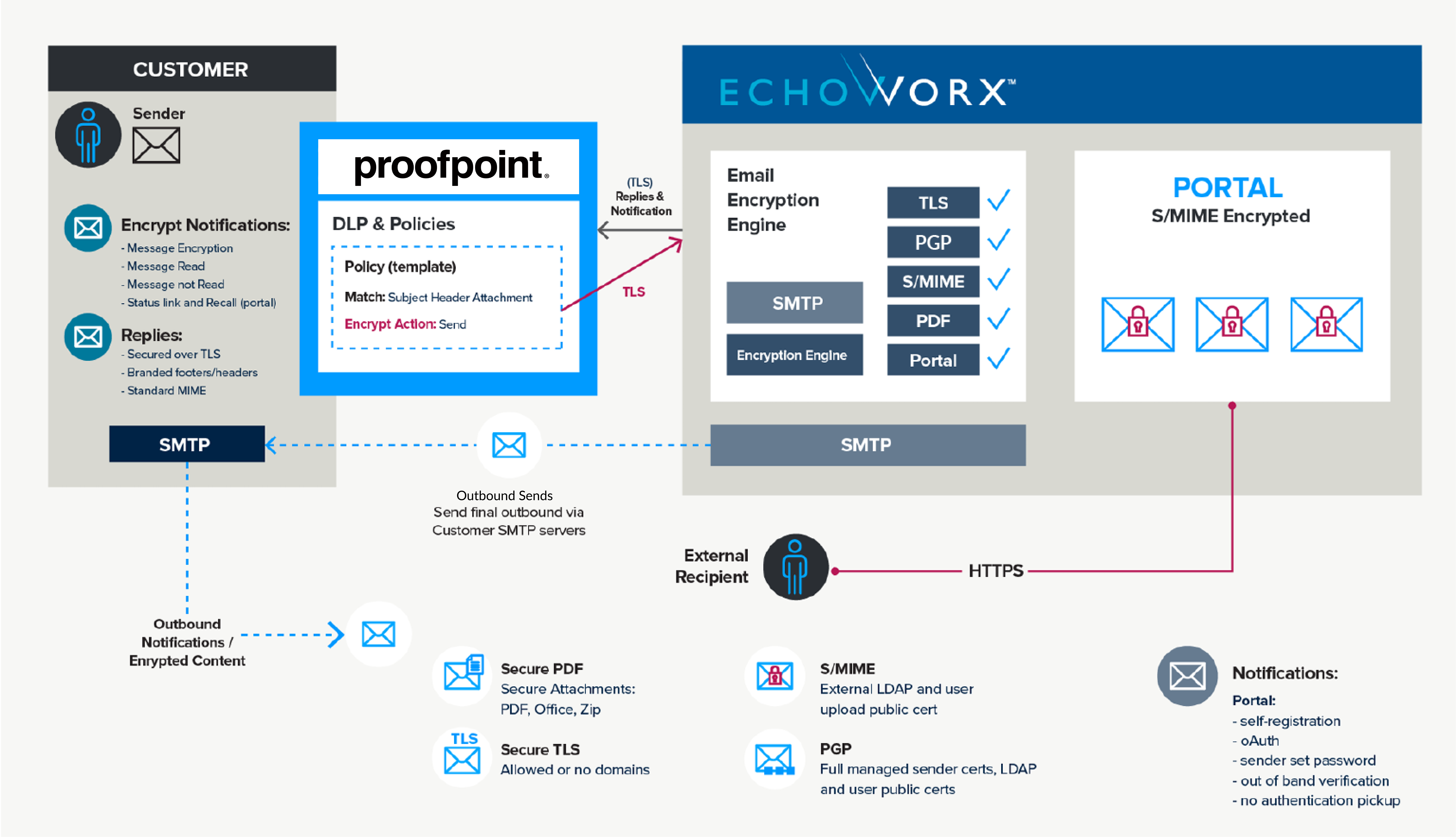
Managing multiple security vendors, such as Microsoft 365, Proofpoint, or Forcepoint, may seem like a necessity, but without seamless integration, these tools create silos, inefficiencies, and—most critically—security gaps. Add in cloud communication platforms like Twilio and DigiCert, KMS solutions, and multi-factor authentication mechanisms, and the result is a tangled web of disconnected systems.
The Hidden Cost of Broken Systems
When security tools fail to integrate, IT teams are stuck firefighting instead of proactively preventing threats. Mimecast’s 2024 State of Email Security report found that 84% of organizations experienced email-based security incidents last year. These incidents often stem from misaligned or poorly integrated tools, causing issues like failed encryption or non-compliance with regulations.
For example, a major financial institution paid an $80 million regulatory fine after failing to encrypt sensitive communications—partly due to interoperability issues with its email security tools. This wasn’t just a technical error; it damaged client trust and the company’s reputation.
Integration Is Now a Strategic Imperative
In today’s complex risk environment, layered security strategies are critical. But layers without integration are like mismatched puzzle pieces. Effective protection requires seamless collaboration between core components like encryption, email security, and data loss prevention (DLP).
Real-world challenges underline this need. An Irish bank recently considered a solution with a message recall feature, only to find it lacked an audit trail—jeopardizing compliance and accountability. This highlights the importance of security solutions designed for transparency and regulatory alignment. Features like audit trails ensure compliance with standards like GDPR while fostering trust.
Scalable, vendor-agnostic encryption technologies are now the norm for global enterprises, reflecting the reality that integration is no longer optional. Organizations risk inefficiencies, compliance failures, and a loss of stakeholder confidence without it.
As one industry leader put it, “The future of security is about transparency and trust. Features like audit trails and real-time notifications are critical to ensuring both security and user confidence.” By prioritizing integration and adaptability, organizations can manage risks, meet compliance requirements, and maintain resilience in an ever-evolving landscape.
Echoworx, Mimecast, and Enterprise Strategy Group break down interoperability and why it matters.
→ Watch full video
Why Smarter Email Security Matters
Email is critical for business communication, but without seamless security integration, it becomes a major vulnerability. Poor implementation leads to problems like undelivered encrypted emails, exposed sensitive data, and compliance failures—issues with costly consequences. According to IBM’s 2024 Cost of a Data Breach report, email compromises cost businesses an average of $4.78 million per breach.
The challenge? Enterprises operate in complex, multi-vendor ecosystems. A U.S. bank, for instance, might manage Microsoft 365, Azure Active Directory, Symantec, Mimecast, Proofpoint, DigiCert, Twilio, Vonage, and more. Misaligned tools in such setups can severely impact operations.
At Echoworx, we ensure security enhances workflows, not disrupts them. Our encryption platform integrates across diverse systems, enforcing policies while maintaining productivity. We secure emails routed via Proofpoint, Mimecast, or Microsoft 365, automate PGP encryption, and integrate with DigiCert for scalable S/MIME certificate management. Beyond this, we enhance security with Twilio-powered SMS notifications and two-factor authentication.
Smart email security isn’t just about compliance—it’s about operational efficiency in a connected, complex world.
Real Solutions Designed for Real Challenges
Our experience shows that adopting vendor-agnostic, scalable encryption solutions can reduce integration challenges by up to 40%. For example, a global healthcare organization using Echoworx improved encrypted email delivery rates by 30% while reducing compliance team workloads. These aren’t abstract promises—they’re quantifiable results rooted in deliberate engineering and real-world application.
Are You Resilient or Just Checking Boxes?
Here’s the bottom line: Is your security strategy truly resilient, or are you just meeting the minimum for compliance? Regulatory adherence alone won’t protect your organization from growing cybersecurity threats. Resilience requires robust encryption coupled with seamless integration, forming a security foundation that supports growth, trust, and operational efficiency.
At Echoworx, resilience is more than a buzzword—it’s our standard. We go beyond compliance to deliver integrated, scalable encryption solutions that empower your organization to thrive in the face of complex, high-stakes challenges.
Isn’t it time your email security worked as hard as you do?
Because in the end, security shouldn’t be something you fight against. It should be something you rely on.
READ MORE: Encryption Features