Security That Moves at the Speed of a Deal

We’ve all seen it happen. A multi-million dollar merger is on the line, the final documents are ready, and the entire deal hinges on one last, secure exchange. The legal team needs to send a critical file to an external party—a senior partner, a C-level executive, someone who has no time for technical nonsense. The clock is ticking. What do you do?
For too long, the answer has been a frustrating compromise between security and speed. You can use the ironclad, corporate-approved encryption portal. The one that demands registration, a new password with 16 characters including a special symbol and the name of your first pet, followed by a multi-step verification dance. Or, you can do what everyone actually does under pressure: attach it to an email and hope for the best.
This is the dirty secret of enterprise security. We build fortresses, but users just dig tunnels underneath them because the front gate is too cumbersome. We’ve designed systems so secure they are practically unusable, forcing the very people we’re trying to protect to become the weakest link. This isn’t a user problem; it’s a design failure. Security that gets in the way of business is bad security.
The Friction Epidemic: When Security Becomes the Bottleneck
In high-stakes environments like mergers and acquisitions, divestitures, or regulatory filings, time is the most valuable currency. Any delay, any friction, can derail a transaction worth millions. The “You Need to Access This… Yesterday” problem is a daily nightmare for IT and security leaders. Your job is to enable the business, but your tools often do the opposite.
The classic secure communication workflow is a case study in operational friction:
- The Portal Problem: You send a secure message. The recipient, an important external executive, gets a link to a portal they’ve never seen before. They’re asked to create an account. They sigh, roll their eyes, and immediately call their assistant—or worse, call you.
- Password Fatigue: The recipient already manages dozens of passwords. Creating another one is an annoyance they will avoid at all costs. They might try to reuse an old password, which is a security risk, or they will simply give up.
- The Support Ticket Spiral: The deal is on hold while your team plays tech support, walking a non-technical user through a password reset or explaining what a “key” is. Meanwhile, the business leaders are asking why things are taking so long. The security team, meant to be a silent guardian, is now the public face of delay.
The result is predictable. Users bypass the system entirely. They turn to shadow IT—consumer-grade file-sharing services or, heaven forbid, unencrypted email. Your carefully constructed security policy, your compliance posture, your peace of mind—all gone in a single click. The paradox is that in our attempt to be 100% secure, we create an environment that is 100% insecure when it matters most.
From Barrier to Accelerator: A New Philosophy
What if we stopped thinking about security as a wall? What if, instead, we designed it to be a lubricant. Something that makes critical business processes run faster and smoother?
True enterprise-grade security shouldn’t be about adding more steps. It should be about removing them. It must adapt to the urgency of the business moment, not fight against it. This requires a fundamental shift in philosophy, moving from complex cryptographic hurdles to simple, human-centric solutions.
The principle is simple: leverage the human layer to enhance security, not to complicate it. Instead of forcing users to navigate complex systems, we can integrate powerful security into workflows they already understand.
The Power of a Simple Conversation: Verification Codes
Consider the M&A scenario again. A document needs to be delivered securely and instantly. Instead of a portal and a password, imagine this:
- The encrypted file is sent.
- A unique, one-time verification code is generated and sent to a designated employee within your organization.
- That employee picks up the phone—a trusted, out-of-band channel—and verbally shares the code with the external recipient.
- The recipient enters the code and gets immediate access.
That’s it. No registration. No password creation. No forgotten credentials.
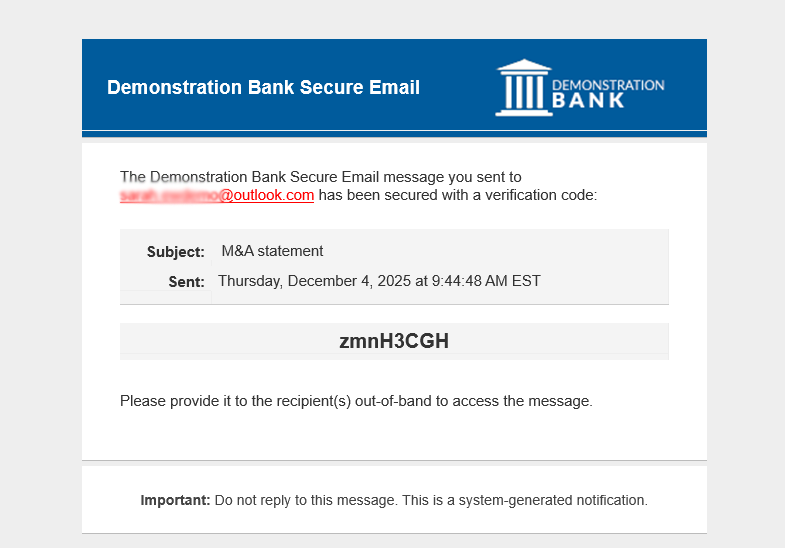
Figure 1: Screenshot of document encryption message using verification code. The sender verbally shares the code with recipient.
This mechanism solves the friction problem while dramatically increasing security. By using a separate, non-digital channel (a phone call) for the second factor of authentication, you bypass entire categories of attack vectors like phishing and credential stuffing. An attacker might intercept the email, but without the verbally communicated code, the data is useless.
It’s a perfect fusion of powerful encryption and elegant, human-centric design. You empower users to work at the speed of the deal without ever forcing them to compromise on security.
Ending the Identity Nightmare: The Role of SSO
This philosophy of reducing friction extends to internal users as well. Your employees are just as susceptible to password fatigue and account overload as external partners. Innovations like OpenID Connect Single Sign-On (SSO) are essential for streamlining access to secure communication platforms.
By integrating with your existing identity provider, you eliminate the need for separate logins and passwords for your encryption gateway. Employees sign in with the same credentials they use for everything else. This not only improves their daily experience but also centralizes access control, making it easier for you to manage permissions and onboard or offboard users. It’s another example of security that works with the user, not against them.
The Strategic Advantage of Zero-Friction Security
For IT and Security Directors, adopting a zero-friction approach moves you from a cost center to a strategic enabler. The benefits impact the core of the business.
- Accelerate High-Value Workflows: When you remove the administrative drag from secure communications, deals close faster. Legal opinions are shared instantly. Financial models are exchanged without delay. This agility is a direct competitive advantage, allowing your organization to outmaneuver competitors still wrestling with clumsy legacy systems.
- Guarantee Compliance Under Pressure: Regulatory frameworks like DORA and NIS 2 demand provable control over your communications. When time is short, the temptation to use non-compliant methods is immense. A zero-friction system ensures that even the most urgent message remains encrypted, authenticated, and auditable. Compliance becomes the default, not an afterthought.
- Eliminate Human Error and Liability: Complexity is the enemy of compliance. When security is simple, adoption soars. Legal teams stop using risky cloud shares. HR transmits sensitive data with confidence. The entire organization’s attack surface shrinks because the secure path is also the easiest path. You move from reactive risk management to proactive operational assurance.
We’ve reached an inflection point where security can no longer be a speed bump on the road to business success. For modern security leaders, the mission is clear: transform encryption from a technical hurdle into an operational accelerator. The future of security is not about building higher walls; it’s about opening the right doors, instantly and securely.
Discover a Smarter Way to Authenticate
Choosing the right authentication method is critical to balancing security with user experience. Just as a single key doesn’t unlock every door, a single authentication method doesn’t fit every business need. From passwordless verification codes for high-stakes external partners to seamless SSO for internal teams, the right approach makes all the difference.
Echoworx offers a suite of flexible authentication options designed to match your specific risk profiles and workflows. By empowering users with choice, you can enhance security, ensure compliance, and eliminate the friction that slows business down.
Ready to see how adaptable authentication can transform your security? Explore Echoworx’s authentication options.
